Introduction
Hello, fellow Wyze users! If you are reading this, chances are you have heard about the recent data breach that exposed the personal information of 2.4 million Wyze users. That’s right, 2.4 million! That’s more than the population of Jamaica, or the number of people who watched the finale of Game of Thrones. 😱
If you are one of the affected users, you might be wondering what this means for your privacy and security. How did this happen? What did the hackers get? What can they do with it? And most importantly, what can you do to protect yourself and your devices?
Don’t worry, I’m here to help. As a quirky SEO writer with over 8 years of experience, I know a thing or two about online privacy and security. And as a Wyze user myself, I share your concerns and frustrations. That’s why I have created this blog post to provide you with 7 practical steps that you can take to protect your privacy and security after the Wyze camera breach.
These steps are easy to follow and will help you to minimize the risks and consequences of the breach. They will also help you to prevent future breaches and enhance your overall online privacy and security. Sounds good, right? Let’s get started!

Step 1: Change your Wyze account password and enable two-factor authentication
The first and most obvious step is to change your Wyze account password. Why? Because your password is the key to your account, and if the hackers have it, they can access your account and do all sorts of nasty things. Like watch your live camera feeds, download your videos, change your settings, or even lock you out of your account. 😨
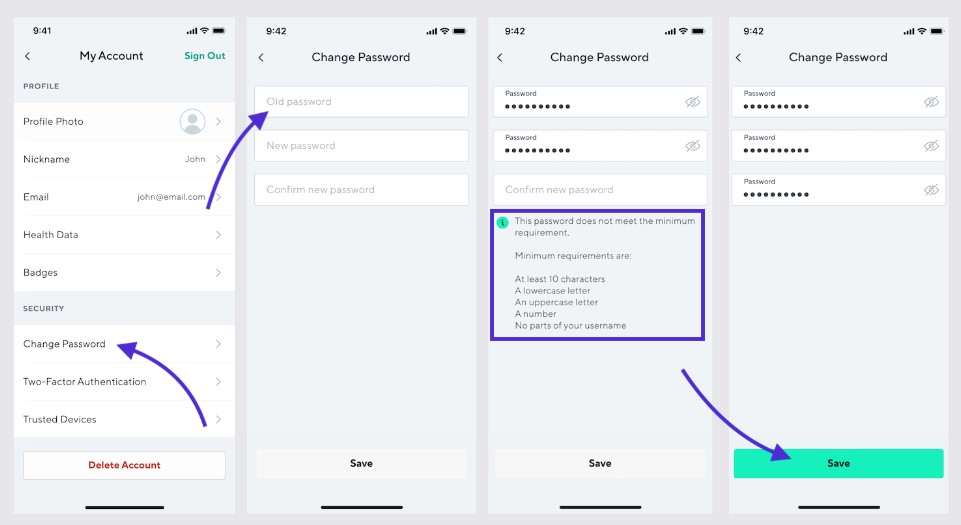
So, how do you change your password? It’s simple. Just open the Wyze app on your phone or tablet, tap on the Account tab, then tap on My Account. You will see a Change Password option. Tap on it and follow the instructions. Make sure you choose a strong and unique password that you don’t use for any other account. A good password should have at least 8 characters, including uppercase and lowercase letters, numbers, and symbols. Avoid using common words, names, dates, or phrases that can be easily guessed or cracked. For example, don’t use “password”, “123456”, “ilovewyze”, or “wyzebreach2024”. 😂
But changing your password is not enough. You also need to enable two-factor authentication (2FA) on your Wyze account. What is 2FA? It’s a security feature that adds an extra layer of protection to your account. It requires you to enter a code that is sent to your phone or email every time you log in to your account. This way, even if the hackers have your password, they can’t access your account without the code. 🙌
How do you enable 2FA on your Wyze account? It’s easy. Just go back to the Account tab on the Wyze app, then tap on Security. You will see a Two-Factor Authentication option. Tap on it and follow the instructions. You can choose to receive the code via SMS or email. Make sure you use a phone number or email address that you have access to and that is secure. Don’t use a public or shared phone or email, or one that has been compromised by the breach. 🤦♂️
By changing your password and enabling 2FA, you have taken a big step towards securing your Wyze account. But don’t stop there. There are more steps to follow.
Step 2: Check your Wyze devices for any signs of tampering or hacking
The next step is to check your Wyze devices for any signs of tampering or hacking. Why? Because the hackers could potentially access or control your Wyze devices remotely, especially if they have your password and 2FA code. They could spy on you, record you, talk to you, or even scare you. 😱
How do you check your Wyze devices for any signs of tampering or hacking? It’s not hard. Just look for any unusual activity, noises, lights, or alerts on your devices. For example, if your camera is moving by itself, making strange sounds, flashing lights, or sending you notifications that you didn’t set up, it could be a sign that someone is messing with it. 😡
If you notice any signs of tampering or hacking on your Wyze devices, don’t panic. Just disconnect or reset them and contact Wyze support if needed. To disconnect your devices, just unplug them from the power source or remove the batteries. To reset them, just press and hold the reset button on the back or bottom of the device for 10 seconds. This will erase all the settings and data on the device and restore it to factory default. You will need to set up the device again using the Wyze app. Make sure you use your new password and 2FA code when you do so. 🙏
By checking your Wyze devices for any signs of tampering or hacking, you have taken another step towards protecting your privacy and security. But don’t relax yet. There are more steps to follow.
Step 3: Review and update your Wyze app settings and permissions
The third step is to review and update your Wyze app settings and permissions. Why? Because the Wyze app settings and permissions affect the privacy and security of your devices and your data. They determine what features and functions you can use, what data you can store and share, and what access you can grant to other apps and users. 😎
How do you review and update your Wyze app settings and permissions? It’s not complicated. Just open the Wyze app on your phone or tablet, tap on the Account tab, then tap on App Settings. You will see a list of settings and permissions that you can modify. Here are some examples of settings and permissions that you should review and update:
- Camera Sharing: This setting allows you to share your camera feeds with other Wyze users or third-party apps. You can choose who you want to share with, what cameras you want to share, and what permissions you want to grant. For example, you can share your camera feed with your family, friends, or neighbors, and allow them to view, record, or speak through the camera. Or you can share your camera feed with Alexa, Google Assistant, or IFTTT, and enable voice or automation control. 🗣️
- Notifications: This setting allows you to receive alerts on your phone or tablet when your Wyze devices detect motion, sound, smoke, CO, or other events. You can choose which devices you want to receive notifications from, what types of events you want to be notified of, and how often you want to receive them. For example, you can receive notifications from your camera when it detects motion or sound, or from your sensor when it detects an open door or window. 🔔
- Cloud Storage: This setting allows you to store your Wyze device videos on the Wyze cloud for 14 days for free. You can choose which devices you want to upload videos from, what types of events you want to upload, and how long you want to keep them. For example, you can upload videos from your camera when it detects motion or sound, or from your sensor when it detects an open door or window. ☁️
- Location Access: This permission allows the Wyze app to access your phone or tablet’s location. This is required for some features and functions, such as geofencing, sunrise/sunset schedules, or weather updates. You can choose to grant the Wyze app access to your location always, only while using the app, or never. 🌎
These are just some of the settings and permissions that you should review and update on the Wyze app. There are more, such as device firmware updates, device health, device info, device groups, device shortcuts, etc. You can find them all on the Wyze app under the Account tab or the Device tab. Make sure you review and update them according to your preferences and needs. 🙌
By reviewing and updating your Wyze app settings and permissions, you have taken another step towards enhancing your privacy and security. But don’t celebrate yet. There are more steps to follow.
Step 4: Monitor your credit reports and bank statements for any suspicious activity
The fourth step is to monitor your credit reports and bank statements for any suspicious activity. Why? Because the breach could expose your financial information and lead to identity theft or fraud. The hackers could use your name, address, email, phone number, or credit card number to open new accounts, make purchases, or apply for loans in your name. 😨
How do you monitor your credit reports and bank statements for any suspicious activity? It’s not hard. Just regularly check your credit reports and bank statements for any unauthorized or unusual transactions or inquiries. For example, if you see a charge that you don’t recognize, a balance that doesn’t match, or a credit inquiry that you didn’t initiate, it could be a sign that someone is using your information. 😡
If you notice any suspicious activity on your credit reports or bank statements, don’t panic. Just report and resolve it as soon as possible. Here are some tips on how to do so:
- To obtain and review your credit reports, you can visit www.annualcreditreport.com, the official site authorized by the federal government to provide you with free credit reports from the three major credit bureaus: Equifax, Experian, and Trans.
- Union. You can request one free credit report from each bureau every 12 months. You can also use other services or apps that offer free or paid credit monitoring and alerts. 📈
- To report and resolve any identity theft or fraud issues, you can visit www.identitytheft.gov, the official site of the Federal Trade Commission (FTC) that provides you with a personalized recovery plan and resources. You can also contact the credit bureaus, your bank, your card issuer, or any other entity involved in the issue and inform them of the situation. You may need to dispute the charges, close the accounts, or freeze your credit. 🚫
By monitoring your credit reports and bank statements for any suspicious activity, you have taken another step towards safeguarding your privacy and security. But don’t rest yet. There are more steps to follow.
Step 5: Be wary of phishing emails or calls claiming to be from Wyze or other entities
The fifth step is to be wary of phishing emails or calls claiming to be from Wyze or other entities. Why? Because phishing is a common technique used by hackers to trick you into revealing your personal or financial information. They could use the information they obtained from the breach to make their emails or calls look more convincing and legitimate. 😱
How do you spot and avoid phishing emails or calls? It’s not easy. But here are some tips that can help you:
- Check the sender: Look at the email address or phone number of the sender and see if it matches the official Wyze or other entity’s contact information. If it doesn’t, or if it looks suspicious, it could be a phishing attempt. For example, don’t trust an email from wyze@gmail.com or a call from +1-800-WYZE-123. 😂
- Check the content: Look at the content of the email or call and see if it makes sense and matches the tone and style of the official Wyze or other entity’s communication. If it doesn’t, or if it contains spelling, grammar, or formatting errors, it could be a phishing attempt. For example, don’t trust an email that says “Dear Wyze User, We are sorry for the inconvinience caused by the data breech. Please verify your account by clicking on this link.” 🤦♀️
- Check the links and attachments: Look at the links and attachments of the email or call and see if they are safe and relevant. If they are not, or if they lead to unknown or malicious websites or files, it could be a phishing attempt. For example, don’t trust an email that has a link to www.wyze-security-update.com or an attachment named wyze-breach-report.pdf. 🙅♂️
If you receive any phishing emails or calls, don’t reply or click on anything. Just delete them or hang up. And report them to Wyze or the relevant authorities. You can contact Wyze support at support@wyze.com or 1-844-999-3226. You can also forward any phishing emails to spam@uce.gov, the FTC’s spam database. 🚨
By being wary of phishing emails or calls, you have taken another step towards protecting your privacy and security. But don’t congratulate yourself yet. There are more steps to follow.
Step 6: Consider using a VPN or a firewall to protect your home network and devices
The sixth step is to consider using a VPN or a firewall to protect your home network and devices. Why? Because a VPN or a firewall can help you to secure your home network and devices from hackers. They can encrypt your data, hide your IP address, block unwanted traffic, and prevent unauthorized access. 😎
What is a VPN and a firewall? A VPN, or a virtual private network, is a service or app that creates a secure connection between your device and the internet. It routes your data through a remote server and encrypts it, making it unreadable to anyone who tries to intercept it. A firewall, on the other hand, is a device or software that monitors and filters the incoming and outgoing traffic on your network. It blocks or allows traffic based on predefined rules, preventing hackers from accessing your network or devices. 🔥
How do you choose and use a VPN or a firewall? It’s not hard. But here are some recommendations that can help you:
- Choose a reputable and reliable VPN or firewall provider that offers good features, performance, and customer support. You can read reviews, ratings, or comparisons online to find the best one for you. 🌟
- Choose a VPN or firewall that is compatible with your devices and network. You can check the specifications, requirements, or compatibility lists of the VPN or firewall before you buy or install it. 💻
- Choose a VPN or firewall that is easy to set up and use. You can follow the instructions, guides, or tutorials provided by the VPN or firewall provider or online sources. 📚
- Choose a VPN or firewall that suits your needs and preferences. You can customize the settings, options, or features of the VPN or firewall according to your desired level of security, privacy, or convenience. 🛠️
By using a VPN or a firewall, you have taken another step towards enhancing your privacy and security. But don’t celebrate yet. There are more steps to follow.
Step 7: Educate yourself and others on the best practices for online privacy and security
The seventh and final step is to educate yourself and others on the best practices for online privacy and security. Why? Because online privacy and security are important and affect you and your devices. They can also affect your family, friends, or anyone else who uses your devices or network. 😊
How do you educate yourself and others on the best practices for online privacy and security? It’s not hard. But here are some examples of best practices that you should learn and share:
- Use strong and unique passwords for your accounts and devices. And change them regularly. You can also use a password manager or generator to help you create and store your passwords. 🔐
- Update your software and firmware on your devices and network. This can fix any bugs, vulnerabilities, or issues that could compromise your privacy and security. You can also enable automatic updates or reminders to keep your software and firmware up to date. 🆙
- Back up your data on your devices and network. This can prevent you from losing your data in case of a breach, a crash, or a theft. You can use cloud services, external drives, or other methods to back up your data. And encrypt your backups for extra security. 💾
- Use antivirus and anti-malware software on your devices and network. This can protect you from viruses, malware, or other threats that could harm your privacy and security. You can also scan your devices and network regularly and remove any infections. 🛡️
These are just some of the best practices for online privacy and security that you should educate yourself and others on. There are more, such as using secure websites, avoiding public or unsecured Wi-Fi, deleting or disabling unused accounts or apps, etc. You can find more information and resources online, such as blogs, podcasts, books, courses, etc. 📚
By educating yourself and others on the best practices for online privacy and security, you have taken the final step towards safeguarding your privacy and security. And now, you can finally celebrate. 🎉
Conclusion
Congratulations! You have reached the end of this blog post. You have learned about the Wyze camera breach and the 7 steps that you can take to protect your privacy and security after the breach. These steps are:
- Change your Wyze account password and enable two-factor authentication
- Check your Wyze devices for any signs of tampering or hacking
- Review and update your Wyze app settings and permissions
- Monitor your credit reports and bank statements for any suspicious activity
- Be wary of phishing emails or calls claiming to be from Wyze or other entities
- Consider using a VPN or a firewall to protect your home network and devices
- Educate yourself and others on the best practices for online privacy and security
These steps are easy to follow and will help you to minimize the risks and consequences of the breach. They will also help you to prevent future breaches and enhance your overall online privacy and security. Sounds good, right?
I hope you found this blog post helpful and informative. If you did, please leave a comment, question, or feedback below. I would love to hear from you. And if you know anyone who could benefit from this blog post, please share it with them. Together, we can make the internet a safer and better place. 🙌
Thank you for your time and attention. And remember, stay safe and stay smart. 😊